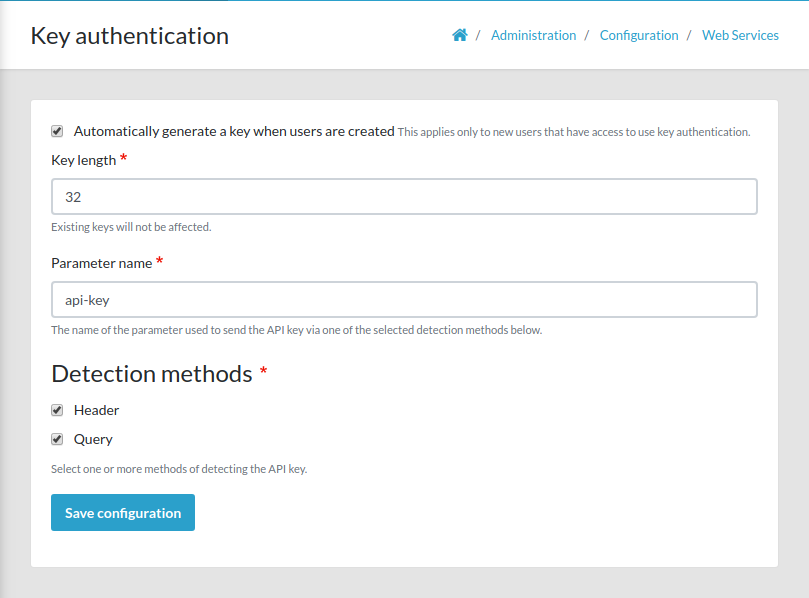
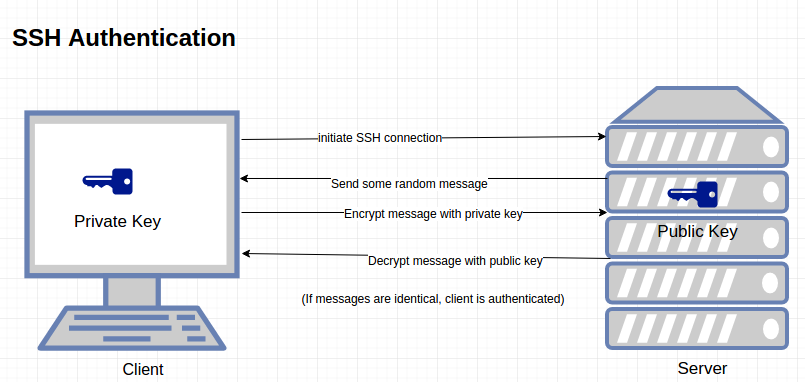
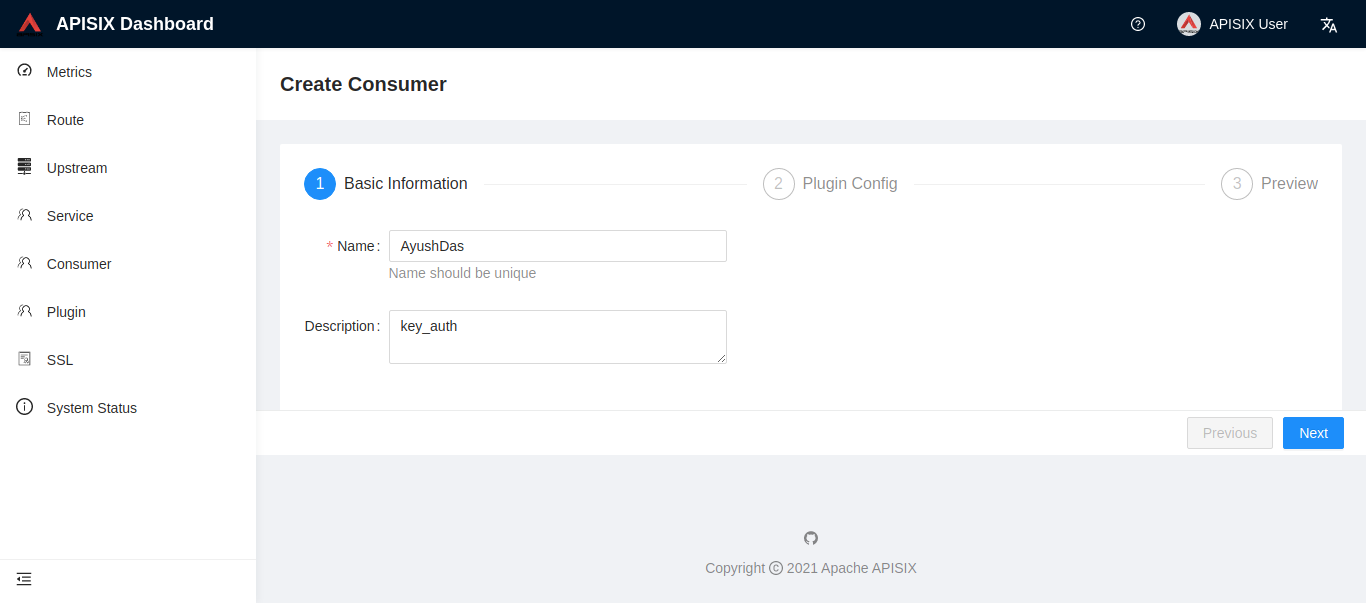
POST request with API key vs. "Make an API Key Auth request". Is there a difference? - Questions & Answers - Make Community
GitHub - KeyAuth/KeyAuth-Source-Code: KeyAuth is an open source authentication system with cloud-hosted solutions available as well.