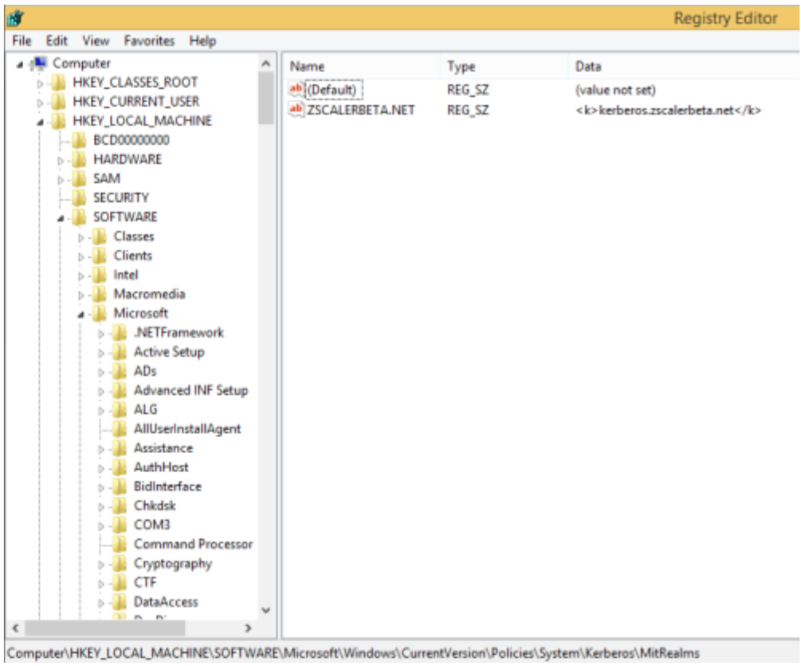
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'Zscaler -windows-1.5.2.7-installer.msi'

Optimizing Content Delivery with Microsoft Delivery Optimization and Zscaler Proxy – All about Microsoft Endpoint Manager

Announcing Zscaler's Terraform Modules for ZIA, ZPA and More: Simplifying and Automating Zscaler Service Deployments | Zscaler
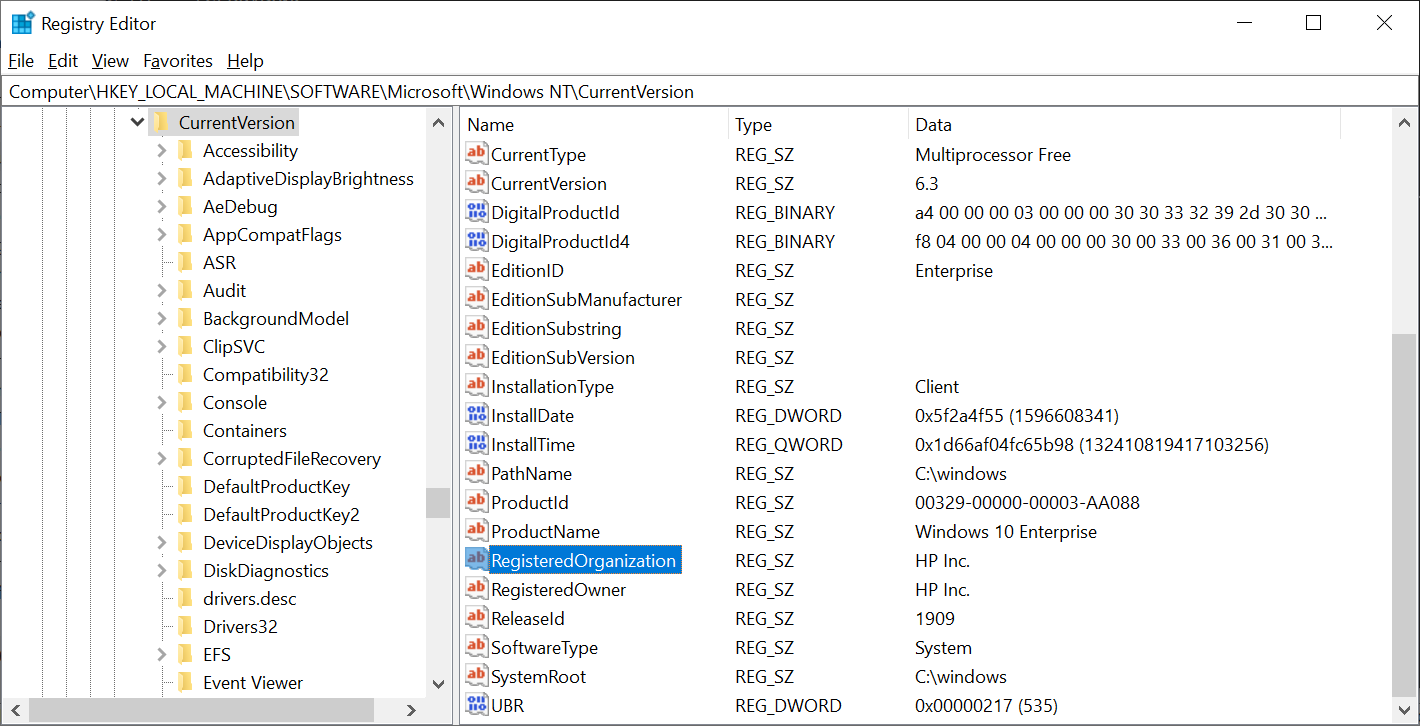
Configuring the Registered Owner and Organization in Windows Autopilot delivered PCs | just another windows noob ?

Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'Zscaler -windows-1.5.2.7-installer.msi'